ATNA tests
This section contains test cases performed with the Gazelle Security Suite tool:
- Link to tool: http://gazelle.ihe.net/gss
- User Guide: https://gazelle.ihe.net/gazelle-documentation/Gazelle-Security-Suite/user.html
- Overview of tool features: recording
- Log in to post comments
11099: Read ATNA Resources page
--> Prior to performing ATNA tests, please read this page for guidelines that address frequently asked questions about testing expectations. <--
THIS PAGE APPLIES TO ATNA TESTING AT 2024 IHE CONNECTATHONs.
- ATNA Requirements
- Gazelle Security Suite (GSS) tool for ATNA testing
- Security Policy (TLS & audit) for the 2022 IHE EU/NA Connectathon
- GSS: Digital Certificates for IHE Connectathons
- GSS: ATNA Questionnaire
- GSS: ATNA Logging Tests - TLS Syslog
- Questions about ATNA testing?
- Evaluation
ATNA Requirements
The ATNA requirements are in the IHE Technical Framework:
- ITI Technical Framework, Vol 1, Section 9 - ATNA Profile.
- ITI Technical Framework Vol 2, for the [ITI-19] and [ITI-20] transactions.
- The RESTful ATNA (Query and Feed) Trial Implementation Supplement specifies additional features.
NOTE: The folloing options were retired in 2021 via CP-ITI-1247 and are no longer tested at IHE Connectathons:
- STX: TLS 1.0 Floor with AES Option
- STX: TLS 1.0 Floor using BCP195 Option
Gazelle Security Suite (GSS) tool for ATNA testing:
Tool-based testing of TLS (node authentication) and of the format and transport of your audit messages is consolidated in one tool - the Gazelle Security Suite (GSS).
- Link to the tool: http://gazelle.ihe.net/gss.
- Instructions for use of the tool are contained in ATNA test descriptions - here.
Security Policy (TLS & audit) for the 2024 IHE EU/NA Connecthon
In order to ensure interoperability between systems doing interoperability (peer-to-peer) testing over TLS (e.g. XDS, XCA...) the Connectathon technical managers have selected a TLS version and ciphers to use for interoperability tests during Connectathon week. (This is analagous to a hospital mandating similar requirements at a given deployment.)
TLS POLICY for [ITI-19]:
*** For IHE Connectathons, interoperabily testing over TLS shall be done using:
- TLS 1.2
- cipher suite - any one of:
- TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- A digital certificate, issued by the Gazelle Security Suite (GSS) tool. See details below.
AUDIT MESSAGE POLICY for [ITI-20]:
Before 2020, an ATNA Audit Record Repository (ARR) was required to support receiving audit messages in both TLS syslog and UDP syslog. That meant that all Secure Node/Applications could send their audit messaes to any ARR.
Now, all actors sending and receiving audit messages may choose to support TLS Syslog, UDP Syslog, and/or FHIR Feed for transport. We expect that the Audit Record Repositories at the NA and EU Connectathons will provide good coverage of the options (TLS, UDP, FHIR), though some ARRs may support a subset. In particular, the FHIR Feed Option in ITI-20 may have less support because it was new as of 2020.
Connectathon technical managers will not select one transport for all audit records exchanged during Connectathon. Instead, Secure Node/Applications will choose ARRs for test partners that are compatible with the audit records they send in ITI-20. Gazelle Test Management will show compatible partners for ITI-20 interoperability tests: "ATNA_Logging_*.
==> GSS: Digital Certificates for IHE Connectathons
The Gazelle Security Suite (GSS) tool is the SINGLE PROVIDER OF DIGITIAL CERTIFICATES for IHE Connectathons.
To obtain a digital certificate from the GSS tool for preparatory & Connectathon testing, follow the instructions in test 11100. That test contains instructions that apply to an IHE Connectathon, whether face-to-face or online.
Some facts about the digital certificates for Connectathon testing:
- The digital certificate you generate in GSS:
- is from Certificate Authority (CA) with a key of 2048 length. You must add the certificate for the new CA in your trust store.
- will contain the fully-qualified domain name (FQDN) of your Connectathon test system. When you use GSS to request the certificate, the tool will prompt you for this value. The FQDN value(s) will be in the subjectAltName entry of your digital certificate. (You may need to provide more than one FQDN when you generate your certificate, e.g., if you will use your system to test TLS connections outside of the Connectathon network, such as using the NIST XDS Tools in your local test lab.)
- Test 11100 contains detailed instructions for generating your certificate, including how to get the fully-qualified domain name for your test system.
- Item (1.b.) means that each system testing TLS transactions during Connectathon week will have a digital certificate that is compatible with the 'FQDN Validation Option' in ATNA. Thus, TLS connections with test partners will work whether the client is performing FQDN validation, or not. This is intentional.
- The certificates are only for testing purposes and cannot be used outside of the IHE Connectathon context.
==> GSS: ATNA Questionnaire
Systems testing ATNA are required to complete the ATNA Questionnaire in the GSS tool, ideally prior to Connectathon week. Embedded in the questionnaire are Audit Record tests and TLS tests customized for the profiles & actors you registered to test at Connectathon.
- Follow instructions in test 11106.
==> GSS: ATNA Logging Tests - ATX: TLS Syslog Option
Read the Technical Framework documentation; you are responsible for all requirements in Record Audit Event [ITI-20] transaction. We will not repeat the requirements here.
WHICH SCHEMA???: The Record Audit Event [ITI-20] specifies use of the DICOM schema for audit messages sent using the ATX: TLS Syslog and ATX: UDP Syslog options. The DICOM schema is found in DICOM Part 15, Section A.5.1.
- The Gazelle Security Suite tool uses the DICOM schema with IHE modifications. The schema used by the GSS tool is: https://gazelle.ihe.net/XSD/IHE/ATNA/dicom_ihe_current.xsd
We expect implementations to be compliant; we have tested audit messages using the DICOM schema at IHE Connectathons since 2016.
- The GSS tool will only provide validation against the DICOM schema. If you fail that test, it is our signal to you that your audit messages are not compliant with the latest DICOM schema. See test 11116.
- We expect interoperability testing at the Connectathon to occur using audit records that are compliant with the DICOM schema.
SENDING AUDIT MESSAGES: You can send your audit records to the GSS tool simulating an Audit Record Repository. See test 11117.
Questions about ATNA Testing?
Contact the Technical Project Manager for the IT Infrastructure domain. Refer to the Contact Us page.
Evaluation
There is no specific evaluation for this test.
Create a text file stating that you found and read the page. Upload that text file into Gazelle Test Management as the Log Return file for test 11099.
- Log in to post comments
11100: Obtain Digital Certificate for TLS Testing
Overview of the test
This test contains instructions for obtaining a digital certificate for your test system that is registered for an IHE Connectathon. You will obtain your digital certificate(s) from the Gazelle Security Suite tool.
Prerequisites for this test
First, please read the ATNA Testing Resources page before proceeding with this test. That page contains important context for using the digital certificates for Connectathon-related tests.
When you generate your digital certificate in Gazelle Security Suite, you will need to know two values:
(1) The hostname(s) for your test system:
- For IHE Connectathons face-to-face: The hostname(s) are assigned to your test system by Gazelle Test Management. (See https://gazelle.ihe.net/TM/ for the 2022 IHE Connectathon; the link may differ for other testing events).
To find the hostname for your test system, log into Gazelle Test Management, then select menu Preparation-->* Network Interfaces. - For IHE Connectathons Online This is the public hostname(s) for your test system. For Connectathons Online, hostname and IP addresses are determined by the operator of the test system. (The operator still shares its hostname(s) with other participants using Gazelle Test Management.)
(2) Domain Name:
- For IHE Connectathons face-to-face: The domain name of the Connectathon network. This information is published by the Technical Manager of each IHE Connectathon. (E.g., for the IHE Connectathon 2022, the Domain Name is ihe-europe.net).
- For IHE Connectathons Online: Your public domain name.
Location Gazelle Security Suite (GSS) tool
Log in to the GSS tool
When logging in to GSS, you will use your username & password from Gazelle Test Management for your Connectathon. There are separate CAS systems for different instances of Gazelle Test Management, and you will have to take this into account when logging in to GSS:
- The European CAS is linked to Gazelle Test Management at http://gazelle.ihe.net/TM/ <---This will be used for the 2022 IHE EU/NA Connectathon
- The North American CAS is linked to Gazelle Test Management at https://gazelle.iheusa.org/gazelle-na/
- If you don't have an account, you can create a new on the Gazelle Test Management home page.
On the GSS home page (http://gazelle.ihe.net/gss) find the "Login" link at the upper right of the page.
- Select either "European Authentication" or "North American Authentication"
- Enter the username and password from either Gazelle Test Management linked above.
Instructions - Obtain a Certificate
- In GSS, select menu PKI-->Request a certificate
- Complete the fields on page:
- Certificate type: Choose "Client and Server" from dropdown list (Required field)
- key size: 2048
- Country (C): (required)
- Organization (O): Your organization name in Gazelle Test Management (Required field)
- Common Name (CN): The Keyword for your test system in Gazelle Test Management (eg EHR_MyMedicalCo) (Required field)
- Title: (optional)
- Given name: (optional)
- Surname: (optional)
- Organizational Unit: (optional)
- eMail: (optiional) email of a technical contact making the request
- Subject Alternative Names:
- You must enter at least one value in this field: the fully-qualified domain name of your test system.
- For a face-to-face Connectathon, this is a combination of the hostname of your test system and the domain name. (See the Prerequisites section above)
- E.g., for Connectathon network, the hostname of your system might be acme0, and the domain name might be ihe-test.net. So, an example of a fully-qualified domain name entered in this field for a digital certificate is acme0.ihe-test.net
- This value may contain additional fully-qualified domain name(s) for your test system when it is operating outside of a face-to-face Connectathon, e.g. when you are testing with the NIST XDS Tools in your home test lab, or if you are participating in an online Connectathon.
- If you have more than one hostname, multiple values are separated by a comma.
- Click the "Request" button.
- You will then be taken to a page listing all requested certificates. Find yours on the top of the list, or use the filters at the top.
- In the "Action" column, click the "View Certificate" (sun) icon. Your certificate details are displayed. Use the "Download" menu to download your certificate and/or the Keystore.
It is also possible to find your certificate using the menu:
- Select menu PKI-->List certificates
- In the "Requester" column, filter the list by entering your username at the top of the column (the username you used to log in to GSS)
- Use the icon in the "Action" column to find and download your certificate, as described above.
You are now ready to use this certificate for performing:
- authentication tests with the Gazelle Security Suite tool
- interoperability (peer-to-peer) tests with your Connectathon partners
Evaluation
There is no specific evaluation for this test.
Create a text file stating that you have requested & received your certificate(s). Upload that text file into Gazelle Test Management as the Log Return file for test 11100.
In subsequent tests (eg 11109 Authentication test), you will verify the proper operation of your test system with your digital certificate.
- Log in to post comments
11106: ATNA Questionnaire
Overview of the test
In this test you complete a form which collects information that will help us evaluate the Audit Logging and Node Authentication (ATNA) capabilities of your test system.
The contents of your ATNA Questionnaire are customized based on the the profiles and actors that you have registered in Gazelle Test Management for a given testing event (e.g. an IHE Connectathon). Depending on which profiles/actors you have registered for, the ATNA Questionnaire will ask you to validate audit messages for transactions you support, and you will be asked to demonstrate successful TLS connections for the transports you support (eg DICOM, MLLP, HTTP).
Prerequisites for this test
Before you can generate your on-line ATNA questionnaire:
- You must have a test system registered in Gazelle Test Management for an upcoming testing event.
- (See https://gazelle.ihe.net/TM/ for the 2022 IHE Connectathon; the link may differ for other testing events).
- Your test system must be registered to test an ATNA actor, e.g., Secure Node, Secure Application, Audit Record Repository.
- Your test system must have a status of "Completed" in Gazelle Test Management.
- This is because the content of the Questionnaire is build based on the profiles & actors you support. We want to know that your registration is complete.
- To check this, log in to Gazelle Test Management.
- Select menu Registration.
- On the System summary tab for your test system, you must set your Registration Status to "Completed" before you start your ATNA Questionnaire.
Location of the ATNA Tools: Gazelle Security Suite (GSS)
Log in to the GSS tool
When logging in to GSS, you will use your username & password from Gazelle Test Management for your testing event. There are separate CAS systems for different instances of Gazelle Test Management, and you will have to take this into account when logging in to GSS:
- The European CAS is linked to Gazelle Test Management at http://gazelle.ihe.net/TM/ <---This will be used for the 2022 IHE EU/NA Connectathon
- The North American CAS is linked to Gazelle Test Management at https://gazelle.iheusa.org/gazelle-na/
- If you don't have an account, you can create a new on the Gazelle Test Management home page.
On the GSS home page (http://gazelle.ihe.net/gss) find the "Login" link at the upper right of the page.
- Select either "European Authentication" or "North American Authentication"
- Enter the username and password from either Gazelle Test Management linked above.
Instructions
1. In GSS, select menu Audit Trail --> ATNA Questionnaires
2. First, search for any existing questionnaires for your organization. Use the filters at the top of the page to search based on various criteria. You will only be able to access the questionnaires created for your organization's test systems. Admins and monitors can access all of them.
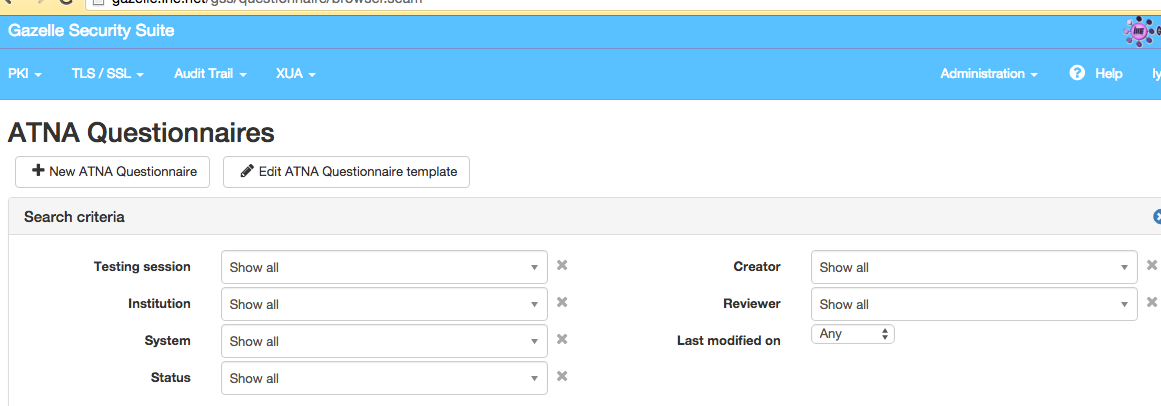
3. You can use the icons in the right 'Actions' column to:
- View the content of the questionnaire
- Edit it
- Delete it (administrators only)
- Review it (monitors only)
![]()
4. If no questionnaire is available for your test system, you need to create a new one.
- Click on the "New ATNA Questionnaire" button
- From the dropdown list, select the name of your test system. Note: If your system doesn't appear...
- ...is your test system registered with status of "Completed"?
- ...are you registered for ATNA Secure Node or Secure Application?
- ...is the testing session closed (ie is the connectathon over)?
- Next, click the "Back to list" button. Use the filter at the top to find your questionnaire in the list. Use the "Edit" icon in the "Action" column to begin.
5. Complete the questionnaire. You are now in the ATNA Questionnaire Editor.
- In the System details, identify the ATNA actor you support. Choose either "Secure Node (SN)" or "Secure Application (SA)"
- Complete the "Inbound network communications" tab
- Complete the "Outbound network communications" tab
- Complete the "Authentication process for local users" tab
- Complete the "Audit messages" tab. This tab is used with test 11116.
- Secure Nodes only: Complete the "Non network means for accessing PHI" tab
- Complete the "TLS Tests" tab. This tab is used with test 11109.
6. Mark your questionnaire "Ready for review"
- When all tabs in the questionnaire are complete, set the Questionnaire's status to "Ready for review" in the "Questionnaire details" section. This is a signal that you have completed your work; we do not want to have monitors evaluating incomplete questionnairs.
Evaluation
Depending on the testing event, the results of this test may be reviewed in advance. More typically, it will be reviewed and graded by a Monitor during the test event itself (e.g. during Connectathon week).
Note: You cannot get connectathon credit (i.e. a "Pass") for your ATNA Secure Node/Application without completing and submitting your questionnaire.
- Log in to post comments
11109: Authentication Test
- Prerequisites
- Overview
- Gazelle Security Suite
- Instructions for clients
- Instructions for servers
- Evaluation
Prerequisites for this test
(1) Read the ATNA Testing Resources page before proceeding with this test.
(2) To perform this test, your digital certificate must be set up on your system (server and/or client). Follow the instructions in test 11000 to obtain digital certificate(s) for your test system(s).
(3) You should create your ATNA Questionnaire (test 11106) prior to running this test.
- The ATNA Questionnaire has a "TLS Tests" tab that identifies the inbound /outbound communications you support.
- That tab determines which of the "Server" and "Client" tests that you must run below.
- You will also record your successful results on that tab.
Overview of the test
In this test, you will use the Gazelle Security Suite (GSS) tool (https://gazelle.ihe.net/gss) to verify that you are able to communicate with TLS clients and servers using digital certificates.
The GSS tool contains multiple client and server simulators that check:
- transport over TLS v1.2, including protocol (DICOM, HL7/MLLP, HTTPS/WS, or syslog)
- cipher suite (TLS_DHE_RSA_WITH_AES_256_GCM_SHA384, and more....),
- certificate authentication
- Digital certificates for pre-Connectathon & Connectathon testing are generated by GSS. See test 11100.
The TLS simulators available in the GSS tool are listed in Column 1 in the following table, along with notes on which you should use for this test:
| Simulator Names (keyword) | To be tested by... |
Simulator configuration |
|
-- Server DICOM TLS 1.2 Floor -- Server HL7 TLS 1.2 Floor -- Server HTTPS/WS TLS 1.2 Floor -- Server Syslog TLS 1.2 Floor |
Connectathon test system that supports the "STX: TLS 1.2 Floor option" and is a client that... -- Initiates a TLS connection with DICOM protocol -- Initiates a TLS connection with MLLP protocol (i.e. HL7 v2 sender) -- Initiates a TLS connection for a webservices transaction -- Initiates a TLS connection to send an audit message over TLS syslog |
TLS 1.2 with 4 'strong' ciphers:
You may test with just one of the ciphers. |
|
-- Server RAW TLS 1.2 INVALID FQDN |
Connectathon test system that is a client supporting the "FQDN Validation of Server Certificate option" |
TLS 1.2 with 4 'strong' ciphers; see list above. Certificate has an invalid value for subjectAltName. |
|
-- Client TLS 1.2 Floor |
Connectathon test system that supports the "STX: TLS 1.2 Floor option" and is a server that... -- Accepts a TLS connection with DICOM protocol -- Accepts a TLS connection with MLLP protocol (i.e. HL7 v2 responder) -- Accepts a TLS connection for a webservices transaction -- Accepts a TLS connection to receive an audit message over TLS syslog |
TLS 1.2 with 4 'strong' ciphers; see list above. |
Location Gazelle Security Suite (GSS) tool:
Log in to the GSS tool
When logging in to GSS, you will use your username & password from Gazelle Test Management for your testing event. There are separate CAS systems for different instances of Gazelle Test Management, and you will have to take this into account when logging in to GSS:
- The European CAS is linked to Gazelle Test Management at http://gazelle.ihe.net/TM/ <---This will be used for the 2022 IHE EU/NA Connectathon
- The North American CAS is linked to Gazelle Test Management at https://gazelle.iheusa.org/gazelle-na/
- If you don't have an account, you can create a new on the Gazelle Test Management home page.
On the GSS home page (http://gazelle.ihe.net/gss) find the "Login" link at the upper right of the page.
- Select either "European Authentication" or "North American Authentication"
- Enter the username and password from either Gazelle Test Management linked above.
Instructions for outbound transactions (Client side is tested)
If your test system (SUT) does not act as a client (i.e., does not initiate any transactions), then skip this portion of the test and only test the Server side below).
If your SUT acts as a client, you must be able to access to TLS server's public IP. You have to test your client by connecting to Server Simulators in the Gazelle Security Suite tool.
1. On the home page for the Gazelle Security Suite, select menu TLS/SSL-->Simulators-->Servers to find the list of server simulators. There are servers for different protocls (DICOM, HL7...) and for different ATNA options (e.g., TLS 1.2 Floor...).
- You will test only the protocols you support -- those listed on the "TLS Tests" tab of your ATNA questionnaire.

2. Configure your client to connect to the test TLS server.
3. Check that the server is started before trying to connect to it. Click on the link for the server you want and look for status "Running"
4. In your SUT, perform a connection (eg send a query) to the test server. The TLS connection is valid, but at transaction level you will get invalid replies because we are only checking for the TLS connection.
5. You should then get a time-stamped entry in the results list at the bottom of the page. Blue dot means OK, red NOT OK.
5. For each successful connection, view the result with the icon in the "Action" column. Copy the Permanent link (URL) to the result into your ATNA Questionnaire, on the "TLS Tests" tab The link must be formatted like https://.../connection.seam?id=...
6. Repeat these steps for each supported protocol (HL7v2 , DICOM, Syslog server ...) : e.g., if your system has no DICOM capabilities, you can skip that portion of the test.
Instructions for inbound transactions (Server side is tested)
If your test system (SUT) does not act as a server (i.e., does not respond to any transactions initiated by others), then skip this portion of the test and only perform the Client test above).
If your SUT acts as a server (i.e. a responder to IHE transactions), your server must be accessible from the outside so that the GSS tool, as a client simulator, can connect to your SUT.
1. On the home page for the Gazelle Security Suite, select menu TLS/SSL-->Simulators-->Clients to find the list of client simulators.
2. In the "Start Connection" section of the page, you will have to specify, for each supported protocol :
- Client type : protocol supported (HL7, DICOM, WS, SYSLOG, or RAW)
- You will test only the protocols you support -- those listed on the "TLS Tests" tab of your ATNA questionnaire.
- Target host : public IP of your server
- Target port : public port of your server
3. Then click on "Start client".
4. You should then get a time-stamped entry in the results list. Blue means OK, red NOT OK.
5. For each successful connection, view the result at the bottom of the page using the icon in the "Actions" column. Copy the Permanent Link (URL) to the result into your ATNA Questionnaire, on the "TLS Tests" tab. The link must be formatted like https://.../connection.seam?id=...
6. Repeat these steps for each supported protocol (HL7v2, DICOM, Syslog client, ...) : e.g., if your system has no DICOM capabilities, you can skip that portion of the test.
Evaluation
Depending on the testing event, the results of this test may be reviewed in advance. More typically, it will be reviewed and graded by a Monitor during the test event itself (e.g. during Connectathon week).
The tool reports success or failure for each test you perform. Your test system must demonstrate successful TLS handshake for each inbound and outbound protocol you support.
If you are performing this test in preparation for an IHE Connectathon, a Connectathon monitor will verify your results as follows. The monitor will:
- Access the TLS tests tab in the ATNA Questionnaire. (The SUT only performs tests for the protocols it supports, and skips the ones not supported.)
- For each "SERVER" tested side :
- The test result must be PASSED.
- During a Connectathon, these items can also be verified:
- the SUT host must be the IP specified in the configuration of the system.
- the SUT port must be the one specified in the configuration of the system for the protocol.
- For each "CLIENT" tested side :
- The connection must succeed (blue dot).
- During a Connectathon, this item can also be verified:
- the host in the SUT address must be the IP specified in the configuration of the system. The port is not verified for outbound transactions.
- During the Connectathon, the monitor may choose to ask the vendor to re-run a test if the results raise questions about the system's support of TLS.
- Log in to post comments
11110: Authentication error cases
Overview of the test
*** If your ATNA Secure Node/Secure Application is only a client (ie it only initiates transactions), then this test case is not applicable for you. Skip it. ***
This test exercises several error cases. You will use the TLS Tool in the Gazelle Security Suite as a simulated client, trying to connect to a Secure Node (SN) or Secure Application (SA) acting as a server.
Prerequisite for this test
Perform test 11109 Authentication Test before running this 'error cases' test.
Location of the ATNA Tools: Gazelle Security Suite
Log in to the GSS tool
When logging in to GSS, you will use your username & password from Gazelle Test Management for your testing event. There are separate CAS systems for different instances of Gazelle Test Management, and you will have to take this into account when logging in to GSS:
- The European CAS is linked to Gazelle Test Management at http://gazelle.ihe.net/TM/ <---This will be used for the 2022 IHE Connectathon
- The North American CAS is linked to Gazelle Test Management at https://gazelle.iheusa.org/gazelle-na/
- If you don't have an account, you can create a new on the Gazelle Test Management home page.
On the GSS home page (http://gazelle.ihe.net/gss) find the "Login" link at the upper right of the page.
- Select either "European Authentication" or "North American Authentication"
- Enter the username and password from either Gazelle Test Management linked above.
Instructions
- Select menu TLS/SSL-->Testing-->Test Cases
- Run each of the error test cases listed:
- IHE_ErrorCase_Corrupted
- IHE_ErrorCase_Expired
- IHE_ErrorCase_Revoked
- IHE_ErrorCase-Self-Signed
- IHE_ErrorCase_Unknown
- IHE_ErrorCase_Without_Authentication
- IHE_ErrorCase_Wrong_Key
- Once you are on the 'Run a test' page, use the 'Client type' dropdown list to select the transport supported on your server (HL7v2, DICOM, HL7, DICOM_ECHO, WEBSERVICE, SYSLOG, or RAW)
- Input the host / IP address and port of your system and click on 'Run'.
- If you implement several transports as a server, you should mix message types over those error test cases in order to have at least one implemented protocol covered by one step. It is not necessary to run each of the test cases for each transport.
- After each test case, find your result in the list of Test Executions.
- Capture the permanent links to your PASSED results. Copy/paste the links into Gazelle Test Management as your results for test 11110.
Evaluation
Depending on the testing event, the results of this test may be reviewed in advance. More typically, it will be reviewed and graded by a Monitor during the test event itself (e.g. during Connectathon week).
Each error case must have a result of 'PASSED'.
Each transport type (HL7v2, DICOM, HL7, DICOM_ECHO, WEBSERVICE, SYSLOG, or RAW) implemented by your system as a server must have been tested at least one time in the list of error cases.
If you are performing this test in preparation for a Connectathon, a Connectathon monitor will verify your results pasted into each test step.
- Log in to post comments
11116: Audit message check
Overview of the test
This test applies to a Secure Node/Application that supports the ATX: TLS Syslog or ATX: TLS UDP Option.
In this test, a Secure Node or Secure Application tests audit messages it sends.
- We use the Gazelle Security Suite (GSS) tool to test the content of the audit message against the schema and against requirements documented in the IHE Technical Framework for some transactions.
- In this test, we do not test the transport of the audit message (TLS or UDP).
The Gazelle Security Suite tool provides the ability to validate audit messages against the DICOM schema and the audit message definitions for many transactions in IHE Technical Frameworks. (We are not longer testing the RFC 3881 schema; the ATNA profile requires support for the DICOM schema for syslog audit messages sent via ITI-20.)
Location of the ATNA Tools: Gazelle Security Suite
- For European Connectathon: http://gazelle.ihe.net/gss
- For North America Connectathon: http://gazelle.iheusa.org/gss
Log in to the GSS tool
When logging in to GSS, you will use your username & password from Gazelle Test Management for your testing event. There are separate CAS systems for different instances of Gazelle Test Management, and you will have to take this into account when logging in to GSS:
If you don't have an account, you can create a new on the Gazelle Test Management home page.
On the GSS home page find the "Login" link at the upper right of the page; enter your Gazelle username and password if asked. If you were already logged into another Gazelle application, GSS will silently login you.
Instructions
You may perform this test directly in the ATNA Questionnaire **or** you may use the Gazelle EVSClient tool. If you are preparing for an IHE Connectathon, you should use the instructions below for the ATNA Questionnaire.
---->Instructions for checking audit messages using the ATNA Questionnaire:
- Create a new ATNA Questionnaire for your test system using the instructions for test 11106.
- Find the Audit Messages tab in the questionnaire. That tab contains "Instructions" and enables you to upload and validate audit messages directly on that tab.
- You should validate all messages that you have marked "Implemented".
- When you are done, find the Permanent Link to the your ATNA Questionnaire. Copy/paste that link into the chat window in Gazelle Test Management for test 11116.
---->Instructions for checking audit messages using the EVSClient tool:
- In the Gazelle EVSClient, select menu IHE-->Audit messages-->Validate
- Select the Add button, and upload the XML file for your audit message
- From the Model based validation dropdown list, select the entry that matches your audit message. (Note that additional validations will be added over time.)
- Select the Validate button.
- You should validate all audit messages associated with functionality & transactions supported by your test system.
- In the Validation Results displayed, find the Permanent Link to the results. Copy/paste the link(s) into the chat window in Gazelle Test Management for 11116.
Evaluation
Depending on the testing event, the results of this test may be reviewed in advance. More typically, it will be reviewed and graded by a Monitor during the test event itself (e.g. during Connectathon week).
The tool reports the results of the validation of your messages. We are looking for PASSED results.
- Log in to post comments
11117: Send audit or event message to Syslog Collector
Overview of the test
In this test, a client sends audit records or event reports using transaction [ITI-20] Record Audit Event to the Syslog Collector tool acting as an Audit Record Repository or Event Repository. The Syslog Collector is one of the tools embedded in the Gazelle Security Suite.
This test is performed by an ATNA Secure Node, Secure Application or Audit Record Forwarder. It is also performed by a SOLE Event Reporter.
Note that this test checks the transport of audit messages. The content of your audit message is verified in a different test.
Location of the ATNA Tools: Gazelle Security Suite (GSS)
Log in to the GSS tool
When logging in to GSS, you will use your username & password from Gazelle Test Management for your testing event. There are separate CAS systems for different instances of Gazelle Test Management, and you will have to take this into account when logging in to GSS:
- The European CAS is linked to Gazelle Test Management at http://gazelle.ihe.net/TM/ <---This will be used for the 2022 IHE Connectathon
- The North American CAS is linked to Gazelle Test Management at https://gazelle.iheusa.org/gazelle-na/
- If you don't have an account, you can create a new on the Gazelle Test Management home page.
On the GSS home page (http://gazelle.ihe.net/gss) find the "Login" link at the upper right of the page.
- Select either "European Authentication" or "North American Authentication"
- Enter the username and password from either Gazelle Test Management linked above.
Instructions
- Access the Syslog Collector in GSS under menu Audit Trail --> Syslog Collector. This page displays the tool's IP address and UPD and TCP-TLS ports.
- Configure your application to send your audit messages (event reports) to the Syslog Collector.
- Then trigger any event that initiate an ITI-20 transaction. This event may be an IHE transaction or other system activity (eg system start/stop or one of the SOLE events). Your system should finally send the message to the Syslog Collector.
- IMPORTANT NOTE: The Syslog Collector tool is a free, shared resource. It is intended for intended for brief, intermittent use. Developers SHOULD NOT configure their system to send syslog messages to the tool on a long-term basis. Flooding the tool with audit messages can make it unavailble for use by others.
Evaluation
You must check that your audit message has been received by the Syslog Collector and that the protocol SYSLOG is correctly implemented.
- Go to Gazelle Security Suite, on page Audit Trail > Syslog Collector.
- Filter the list of received messages by the host or the IP of the sender, and find the message you sent according to the timestamps.
- Click on the magnifying glass to display the message details.
- If the protocol is UDP or TLS, if there is a message, a message content, no errors and RFC5424 parsing succeeeded, then the test is successful. There is an example screenshot below.
- Copy the URL to your successful result and paste it into your local Gazelle Test Management as the Log Return file for test 11117.
- Do not forget to stop sending audit-messages to the Syslog Collector once you’ve finished the test. If your system sends a large amount of messages, administrators of the tool may decide to block all your incoming transactions to prevent spam.
Tips
TCP Syslog is using the same framing requirement as TLS Syslog. You can first use the TCP port of Syslog Collector to debug your implementation. Keep in mind that the IHE ATNA Profile expects at least UDP or TLS for actors that produce SYSLOG messages.
 .
.
- Log in to post comments
11118: AuditEvent Resource check
THIS TEST IS UNDER CONSTRUCTION AND NOT YET AVAILABLE...
Overview of the test
This test applies to a Secure Node/Application that supports the ATX: FHIR Feed Option.
The RESTful ATNA TI Supplement, Section 3.20.4.2.2.1, defines a mapping between DICOM Audit Messages and FHIR AuditEvent Resources. Implementers should be creating their AuditEvent Resources according to the defined mappings, and expect that they will be examined according those mappings at IHE Connecthons.
- In test EVS_FHIR_Resource_Validation, a Secure Node or Secure Applicationis asked to use the Gazelle EVSClient tool to test the content of the AuditEvent Resource against the baseline FHIR Requirements.
- In this AuditEventResource check test: Gazelle tools will be enhanced to provide additional validation of AuditResource based on constraints in [ITI-20]. The RESTful ATNA TI Supplement, Section 3.20.4.2.2.1.That mapping will enable Gazelle tooling to verify specifics of the IHE-defined audit records that are sent as FHIR AuditEvent Resources.
Instructions
---->Instructions for checking additional constraints on AuditEvent Resources (mapping defifned in ITI TF-2b: 3.20.4.2.2.1):
- Instructions TBD when tool update is complete.
Evaluation
Depending on the testing event, the results of this test may be reviewed in advance. More typically, it will be reviewed and graded by a Monitor during the test event itself (e.g. during Connectathon week).
The tool reports the results of the validation of your Resources. We are looking for PASSED results.
- Log in to post comments