This documentation is deprecated. A new version of the Gazelle STS tool is available and its documentation is available at https://gazelle.ihe.net/gazelle-documentation/Gazelle-STS/user.html
Introduction
A Security Token Service (STS) is a Web service that issues security tokens according to the WS-Security protocol. It is a standard component of security network that enables actions like: authentication, identity validation or security token exchange.
The primary use of a STS is to acquire SAML tokens in order to request a service in a different security domain.
A SAML assertion in WS-Trust is the kind of security token that provides our STS.
The Web Service Description Language (WSDL) needed to contact our Web service with SOAP and XML Schema is linked below.
Service URL : https://gazelle.ihe.net/picketlink-sts?wsdl
An authentication is asked for this server. The password is connectathon and the username depends on the kind of assertion you are expecting (see table below). The default username is Xuagood.
The animation hereunder explains the different steps when a requestor need information from a service provider using a STS :
This STS is used as part of the Connectathons in NA and EU. Our X-Assertion Provider is configured with a Certificate signed by IHE Europe CA. It is available here https://gazelle.ihe.net/gss/certificate/view.seam?id=1120. It is only configured to help you perform all XUA tests, and hence does not provide token for a different context. As a user of the service you must trust that certificate.
ISSUE TRACKER
If you encounter any issue with this application, report it to our developer team !
A development team works each day to improve this application and fix notified issues. It is very easy and fast to report an issue, and this is the best way to get it fixed as soon as possible. You just need to create an account on our Issue Tracker (link below) and to report it with its resolution priority.
Click on that link to report a problem : http://gazelle.ihe.net/jira/projects/TLS and create an issue with the components "XUA simulation" or "XUA validation". |
Examples of common queries
/!\ In your web service application for service-oriented artchitecture (SOAP), for each request you have to configure the option that enable the line break. In the software SaopUI, the option is "Strip whitespaces = true". If not configured, following requests will not work. /!\
Here is a link to download a valid SoapUI 5.0.0 project with all following requests : Project SoapUI 5.0.0 - Examples queries
(Right-click the link, select “Save target as” or “Save link as.”)
1/ Requesting a Security Token
A requestor sends a request, and if the policy permits, the requestor receives a security token response. An authentication with a username and a password is needed to process the request. They can be changed in tags <wsse:Username> and <wsse:Password>. The password is "connectathon" and the username depends of the kind of assertion that you expect. In the following table, you will find all types of assertions needed for the connectathon with corresponding parameters (don't forget to scroll right to see all parameters). Use the NameID as username to get the desired assertion from the STS. For a default assertion, use the username : "Xuagood".
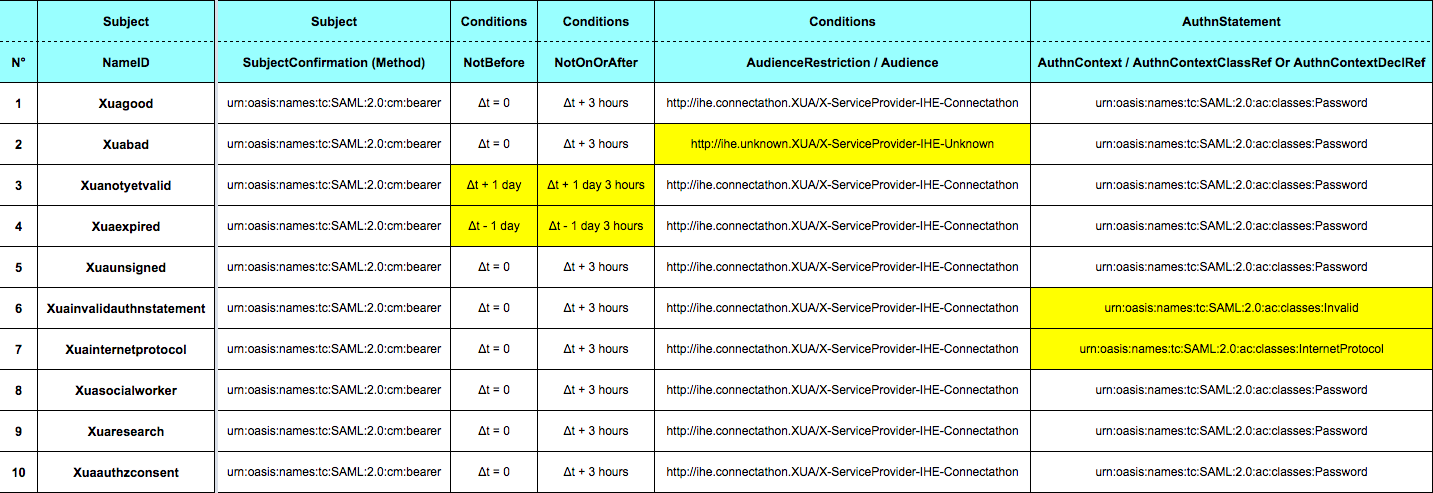
|
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope">
<soap:Header>
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd" env:mustUnderstand="true">
<wsse:UsernameToken wsu:Id="UsernameToken-1">
<wsse:Username>Xuagood</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText" xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">connectathon</wsse:Password>
<wsse:Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">JpQqP2iLrH9DbvaX0GAO9g==</wsse:Nonce>
</wsse:UsernameToken>
</wsse:Security>
<Action xmlns="http://www.w3.org/2005/08/addressing" soap:mustUnderstand="true">http://docs.oasis-open.org/ws-sx/ws-trust/200512/RST/Issue</Action>
<MessageID xmlns="http://www.w3.org/2005/08/addressing" soap:mustUnderstand="true">urn:uuid:9901f17a-14c4-4dc0-a639-132b96d5fd0d</MessageID>
<To xmlns="http://www.w3.org/2005/08/addressing" soap:mustUnderstand="true">https://gazelle.ihe.net/picketlink-sts</To>
<ReplyTo xmlns="http://www.w3.org/2005/08/addressing" soap:mustUnderstand="true">
<Address>http://www.w3.org/2005/08/addressing/anonymous</Address>
</ReplyTo>
</soap:Header>
<soap:Body>
<wst:RequestSecurityToken xmlns:wst="http://docs.oasis-open.org/ws-sx/ws-trust/200512">
<wst:RequestType>http://docs.oasis-open.org/ws-sx/ws-trust/200512/Issue</wst:RequestType>
<wsp:AppliesTo xmlns:wsp="http://www.w3.org/ns/ws-policy">
<wsa:EndpointReference xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsa:Address>http://ihe.connectathon.XUA/X-ServiceProvider-IHE-Connectathon</wsa:Address>
</wsa:EndpointReference>
</wsp:AppliesTo>
<wst:TokenType>http://docs.oasis-open.org/wss/oasis-wss-saml-token-profile-1.1#SAMLV2.0</wst:TokenType>
</wst:RequestSecurityToken>
</soap:Body>
</soap:Envelope>
|
In the response from the web service, if everything worked fine, you should receive an assertion in the tag <saml:Assertion> ... </saml:Assertion> (the opening tag may looks like <saml:Assertion ID="ID_420d4acb-a582-44ab-bba5-52514857c62f" IssueInstant="2015-03-16T16:05:57.406Z" Version="2.0" xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"> ).
The lifetime of a token is 3 hours.
2/ Renew a Security Token
If your previous token expired, you can renew it and get the same token with new expiration semantics. An authentication with an username and a password is needed to proceed the request. They can be changed in tags <wsse:Username> and <wsse:Password> (currently "Xuagood" as username and "connectathon" as password). Copy/paste your assertion achieved from the response of a requesting security token (Part 1 in this tutorial) in the indicated area on the following code. Don't forget to copy information from the opening tag <saml:Assertion ... >.
|
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope">
<soap:Header>
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd" soap:mustUnderstand="true">
<wsse:UsernameToken wsu:Id="UsernameToken-1">
<wsse:Username>Xuagood</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">connectathon</wsse:Password>
<wsse:Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">1S0diJqtjPm78XodEjcwKQ==</wsse:Nonce>
</wsse:UsernameToken>
</wsse:Security>
<Action xmlns="http://www.w3.org/2005/08/addressing" soap:mustUnderstand="true">http://docs.oasis-open.org/ws-sx/ws-trust/200512/RST/Issue</Action>
<MessageID xmlns="http://www.w3.org/2005/08/addressing" soap:mustUnderstand="true">urn:uuid:9901f17a-14c4-4dc0-a639-132b96d5fd0d</MessageID>
<To xmlns="http://www.w3.org/2005/08/addressing" soap:mustUnderstand="true">https://gazelle.ihe.net/picketlink-sts</To>
<ReplyTo xmlns="http://www.w3.org/2005/08/addressing" soap:mustUnderstand="true">
<Address>http://www.w3.org/2005/08/addressing/anonymous</Address>
</ReplyTo>
</soap:Header>
<soap:Body>
<wst:RequestSecurityToken xmlns:wst="http://docs.oasis-open.org/ws-sx/ws-trust/200512">
<wst:RequestType>http://docs.oasis-open.org/ws-sx/ws-trust/200512/Renew</wst:RequestType>
<wst:TokenType>http://docs.oasis-open.org/wss/oasis-wss-saml-token-profile-1.1#SAMLV2.0</wst:TokenType>
<wst:RenewTarget>
<saml:Assertion ... >
/!\ INSERT YOU ASSERTION HERE /!\
</saml:Assertion>
</wst:RenewTarget>
</wst:RequestSecurityToken>
</soap:Body>
</soap:Envelope>
|
In the response from the web service, if everything worked fine, you should receive a new assertion in the tag <saml:Assertion> ... </saml:Assertion> (the opening tag may looks like <saml:Assertion ID="ID_420d4acb-a582-44ab-bba5-52514857c62f" IssueInstant="2015-03-16T16:05:57.406Z" Version="2.0" xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"> ).
The lifetime of a new token is 3 hours.
3/ Cancel a Security Token
If your previous token is no longer needed, you can cancel it in order to terminate its use. Once an assertion is canceled, you cannot renew it. An authentication with a username and a password is needed to proceed the request. They can be changed in tags <wsse:Username> and <wsse:Password> (currently "Xuagood" as username and "connectathon" as password). Copy/paste your assertion received from the response of a requesting security token (Part 1 or Part 2 in this tutorial) in the indicated area on the following code. Don't forget to copy information from the opening tag <saml:Assertion ... >.
|
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope">
<soap:Header>
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd" env:mustUnderstand="true">
<wsse:UsernameToken wsu:Id="UsernameToken-1">
<wsse:Username>Xuagood</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">connectathon</wsse:Password>
<wsse:Nonce EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">1S0diJqtjPm78XodEjcwKQ==</wsse:Nonce>
</wsse:UsernameToken>
</wsse:Security>
<Action xmlns="http://www.w3.org/2005/08/addressing" soap:mustUnderstand="true">http://docs.oasis-open.org/ws-sx/ws-trust/200512/RST/Issue</Action>
<MessageID xmlns="http://www.w3.org/2005/08/addressing" soap:mustUnderstand="true">urn:uuid:9901f17a-14c4-4dc0-a639-132b96d5fd0d</MessageID>
<To xmlns="http://www.w3.org/2005/08/addressing" soap:mustUnderstand="true">https://gazelle.ihe.net/picketlink-sts</To>
<ReplyTo xmlns="http://www.w3.org/2005/08/addressing" soap:mustUnderstand="true">
<Address>http://www.w3.org/2005/08/addressing/anonymous</Address>
</ReplyTo>
</soap:Header>
<soap:Body>
<wst:RequestSecurityToken xmlns:wst="http://docs.oasis-open.org/ws-sx/ws-trust/200512">
<wst:RequestType>http://docs.oasis-open.org/ws-sx/ws-trust/200512/Cancel</wst:RequestType>
<wst:TokenType>http://docs.oasis-open.org/wss/oasis-wss-saml-token-profile-1.1#SAMLV2.0</wst:TokenType>
<wst:CancelTarget>
<saml:Assertion ... >
/!\ INSERT YOU ASSERTION HERE /!\
</saml:Assertion>
</wst:CancelTarget>
</wst:RequestSecurityToken>
</soap:Body>
</soap:Envelope>
|
In the response from the web service, if everything worked fine, you should receive a tag <wst:RequestedTokenCandelled/>.
4/ Validate a Security Token
When you get a security token from a requestor, you may have to validate the assertion. No authentication is needed in this part. Copy/paste the assertion from the request in the indicated area on the following code. Don't forget to copy information from the opening tag <saml:Assertion ... >.
|
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope">
<soap:Header>
<Action xmlns="http://www.w3.org/2005/08/addressing" soap:mustUnderstand="true">http://docs.oasis-open.org/ws-sx/ws-trust/200512/RST/Issue</Action>
<MessageID xmlns="http://www.w3.org/2005/08/addressing" soap:mustUnderstand="true">urn:uuid:9901f17a-14c4-4dc0-a639-132b96d5fd0d</MessageID>
<To xmlns="http://www.w3.org/2005/08/addressing" soap:mustUnderstand="true">https://gazelle.ihe.net/picketlink-sts</To>
<ReplyTo xmlns="http://www.w3.org/2005/08/addressing" soap:mustUnderstand="true">
<Address>http://www.w3.org/2005/08/addressing/anonymous</Address>
</ReplyTo>
</soap:Header>
<soap:Body>
<wst:RequestSecurityToken xmlns:wst="http://docs.oasis-open.org/ws-sx/ws-trust/200512">
<wst:RequestType>http://docs.oasis-open.org/ws-sx/ws-trust/200512/Validate</wst:RequestType>
<wst:TokenType>http://docs.oasis-open.org/wss/oasis-wss-saml-token-profile-1.1#SAMLV2.0</wst:TokenType>
<wst:ValidateTarget>
<saml:Assertion ... >
/!\ INSERT YOU ASSERTION HERE /!\
</saml:Assertion>
</wst:ValidateTarget>
</wst:RequestSecurityToken>
</soap:Body>
</soap:Envelope>
|
In the response from the web service, you should receive a reply with the approval or the rejection of the request.


